# Packages
# README
codebase - A code review dog who keeps your codebase healthy.
codebase provides a way to post review comments to code hosting services, such as GitHub, automatically by integrating with any linter tools with ease. It uses an output of lint tools and posts them as a comment if findings are in the diff of patches to review.
codebase also supports running in the local environment to filter the output of lint tools by diff.
Table of Contents
- Installation
- Input Format
- Code Suggestions
- codebase config file
- Reporters
- Reporter: Local (-reporter=local) [default]
- Reporter: GitHub Checks (-reporter=github-pr-check)
- Reporter: GitHub Checks (-reporter=github-check)
- Reporter: GitHub PullRequest review comment (-reporter=github-pr-reviewe)
- Reporter: GitLab MergeRequest discussions (-reporter=gitlab-mr-discussion)
- Reporter: GitLab MergeRequest commit (-reporter=gitlab-mr-commit)
- Reporter: Bitbucket Code Insights Reports (-reporter=bitbucket-code-report)
- Supported CI services
- Exit codes
- Filter mode
- Articles
Installation
# Install the latest version. (Install it into ./bin/ by default).
$ curl -sfL https://raw.githubusercontent.com/khulnasoft/codebase/master/install.sh | sh -s
# Specify installation directory ($(go env GOPATH)/bin/) and version.
$ curl -sfL https://raw.githubusercontent.com/khulnasoft/codebase/master/install.sh | sh -s -- -b $(go env GOPATH)/bin [vX.Y.Z]
# In alpine linux (as it does not come with curl by default)
$ wget -O - -q https://raw.githubusercontent.com/khulnasoft/codebase/master/install.sh | sh -s [vX.Y.Z]
Nightly releases
You can also use nightly codebase release to try the latest codebase improvements every day!
$ curl -sfL https://raw.githubusercontent.com/khulnasoft/nightly/master/install.sh | sh -s -- -b $(go env GOPATH)/bin
GitHub Action: codebase/action-setup
steps:
- uses: codebase/action-setup@v1
with:
codebase_version: latest # Optional. [latest,nightly,v.X.Y.Z]
homebrew / linuxbrew
You can also install codebase using brew:
$ brew install codebase/tap/codebase
$ brew upgrade codebase/tap/codebase
Scoop on Windows
> scoop install codebase
Build with go install
$ go install github.com/khulnasoft/codebase/cmd/codebase@latest
Input Format
'errorformat'
codebase accepts any compiler or linter result from stdin and parses it with scan-f like 'errorformat', which is the port of Vim's errorformat feature.
For example, if the result format is {file}:{line number}:{column number}: {message},
errorformat should be %f:%l:%c: %m and you can pass it as -efm arguments.
$ golint ./...
comment_iowriter.go:11:6: exported type CommentWriter should have comment or be unexported
$ golint ./... | codebase -efm="%f:%l:%c: %m" -diff="git diff FETCH_HEAD"
| name | description |
|---|---|
| %f | file name |
| %l | line number |
| %c | column number |
| %m | error message |
| %% | the single '%' character |
| ... | ... |
Please see codebase/errorformat and :h errorformat if you want to deal with a more complex output. 'errorformat' can handle more complex output like a multi-line error message.
You can also try errorformat on the Playground!
With this 'errorformat' feature, codebase can support any tool output with ease.
Available pre-defined 'errorformat'
But, you don't have to write 'errorformat' in many cases. codebase supports pre-defined errorformat for major tools.
You can find available errorformat name by codebase -list and you can use it
with -f={name}.
$ codebase -list
golint linter for Go source code - https://github.com/golang/lint
govet Vet examines Go source code and reports suspicious problems - https://golang.org/cmd/vet/
sbt the interactive build tool - http://www.scala-sbt.org/
...
$ golint ./... | codebase -f=golint -diff="git diff FETCH_HEAD"
You can add supported pre-defined 'errorformat' by contributing to codebase/errorformat
Codebase Diagnostic Format (RDFormat)
codebase supports Codebase Diagnostic Format (RDFormat) as a generic diagnostic format and it supports both rdjson and rdjsonl formats.
This rdformat supports rich features like multiline ranged comments, severity, rule code with URL, and code suggestions.
$ <linter> | <convert-to-rdjson> | codebase -f=rdjson -reporter=github-pr-reviewe
# or
$ <linter> | <convert-to-rdjsonl> | codebase -f=rdjsonl -reporter=github-pr-reviewe
Example: ESLint with RDFormat

You can use eslint-formatter-rdjson
to output rdjson as eslint output format.
$ npm install --save-dev eslint-formatter-rdjson
$ eslint -f rdjson . | codebase -f=rdjson -reporter=github-pr-reviewe
Or you can also use codebase/action-eslint for GitHub Actions.
Diff

codebase supports diff (unified format) as an input format especially useful for code suggestions. codebase can integrate with any code suggestions tools or formatters to report suggestions.
-f.diff.strip: option for -f=diff: strip NUM leading components from diff file names (equivalent to 'patch -p') (default is 1 for git diff) (default 1)
$ <any-code-fixer/formatter> # e.g. eslint --fix, gofmt
$ TMPFILE=$(mktemp)
$ git diff >"${TMPFILE}"
$ git stash -u && git stash drop
$ codebase -f=diff -f.diff.strip=1 -reporter=github-pr-reviewe < "${TMPFILE}"
Or you can also use codebase/action-suggester for GitHub Actions.
If diagnostic tools support diff output format, you can pipe the diff directly.
$ gofmt -s -d . | codebase -name="gofmt" -f=diff -f.diff.strip=0 -reporter=github-pr-reviewe
$ shellcheck -f diff $(shfmt -f .) | codebase -f=diff
checkstyle format
codebase also accepts checkstyle XML format as well. If the linter supports checkstyle format as a report format, you can use -f=checkstyle instead of using 'errorformat'.
# Local
$ eslint -f checkstyle . | codebase -f=checkstyle -diff="git diff"
# CI (overwrite tool name which is shown in review comment by -name arg)
$ eslint -f checkstyle . | codebase -f=checkstyle -name="eslint" -reporter=github-check
Also, if you want to pass other Json/XML/etc... format to codebase, you can write a converter.
$ <linter> | <convert-to-checkstyle> | codebase -f=checkstyle -name="<linter>" -reporter=github-pr-check
SARIF format
codebase supports SARIF 2.1.0 JSON format. You can use codebase with -f=sarif option.
# Local
$ eslint -f @microsoft/eslint-formatter-sarif . | codebase -f=sarif -diff="git diff"
Code Suggestions


codebase supports code suggestions feature with rdformat or diff input. You can also use codebase/action-suggester for GitHub Actions.
codebase can suggest code changes along with diagnostic results if a diagnostic tool supports code suggestions data. You can integrate codebase with any code fixing tools and any code formatter with diff input as well.
Code Suggestions Support Table
Note that not all reporters provide support for code suggestions.
-reporter | Suggestion support |
|---|---|
local | NO [1] |
github-check | NO [2] |
github-pr-check | NO [2] |
github-pr-reviewe | OK |
gitlab-mr-discussion | NO [1] |
gitlab-mr-commit | NO [2] |
gerrit-change-review | NO [1] |
bitbucket-code-report | NO [2] |
gitea-pr-review | NO [2] |
- [1] The reporter service supports the code suggestion feature, but codebase does not support it yet. See #678 for the status.
- [2] The reporter service itself doesn't support the code suggestion feature.
codebase config file
codebase can also be controlled via the .codebase.yml configuration file instead of "-f" or "-efm" arguments.
With .codebase.yml, you can run the same commands for both CI service and local environment including editor integration with ease.
.codebase.yml
runner:
<tool-name>:
cmd: <command> # (required)
errorformat: # (optional if you use `format`)
- <list of errorformat>
format: <format-name> # (optional if you use `errorformat`. e.g. golint,rdjson,rdjsonl)
name: <tool-name> # (optional. you can overwrite <tool-name> defined by runner key)
level: <level> # (optional. same as -level flag. [info,warning,error])
# examples
golint:
cmd: golint ./...
errorformat:
- "%f:%l:%c: %m"
level: warning
govet:
cmd: go vet -all .
format: govet
your-awesome-linter:
cmd: awesome-linter run
format: rdjson
name: AwesomeLinter
$ codebase -diff="git diff FETCH_HEAD"
project/run_test.go:61:28: [golint] error strings should not end with punctuation
project/run.go:57:18: [errcheck] defer os.Setenv(name, os.Getenv(name))
project/run.go:58:12: [errcheck] os.Setenv(name, "")
# You can use -runners to run only specified runners.
$ codebase -diff="git diff FETCH_HEAD" -runners=golint,govet
project/run_test.go:61:28: [golint] error strings should not end with punctuation
# You can use -conf to specify config file path.
$ codebase -conf=./.codebase.yml -reporter=github-pr-check
Output format for project config based run is one of the following formats.
<file>: [<tool name>] <message><file>:<lnum>: [<tool name>] <message><file>:<lnum>:<col>: [<tool name>] <message>
Reporters
codebase can report results both in the local environment and review services as continuous integration.
Reporter: Local (-reporter=local) [default]
codebase can find newly introduced findings by filtering linter results
using diff. You can pass the diff command as -diff arg.
$ golint ./... | codebase -f=golint -diff="git diff FETCH_HEAD"
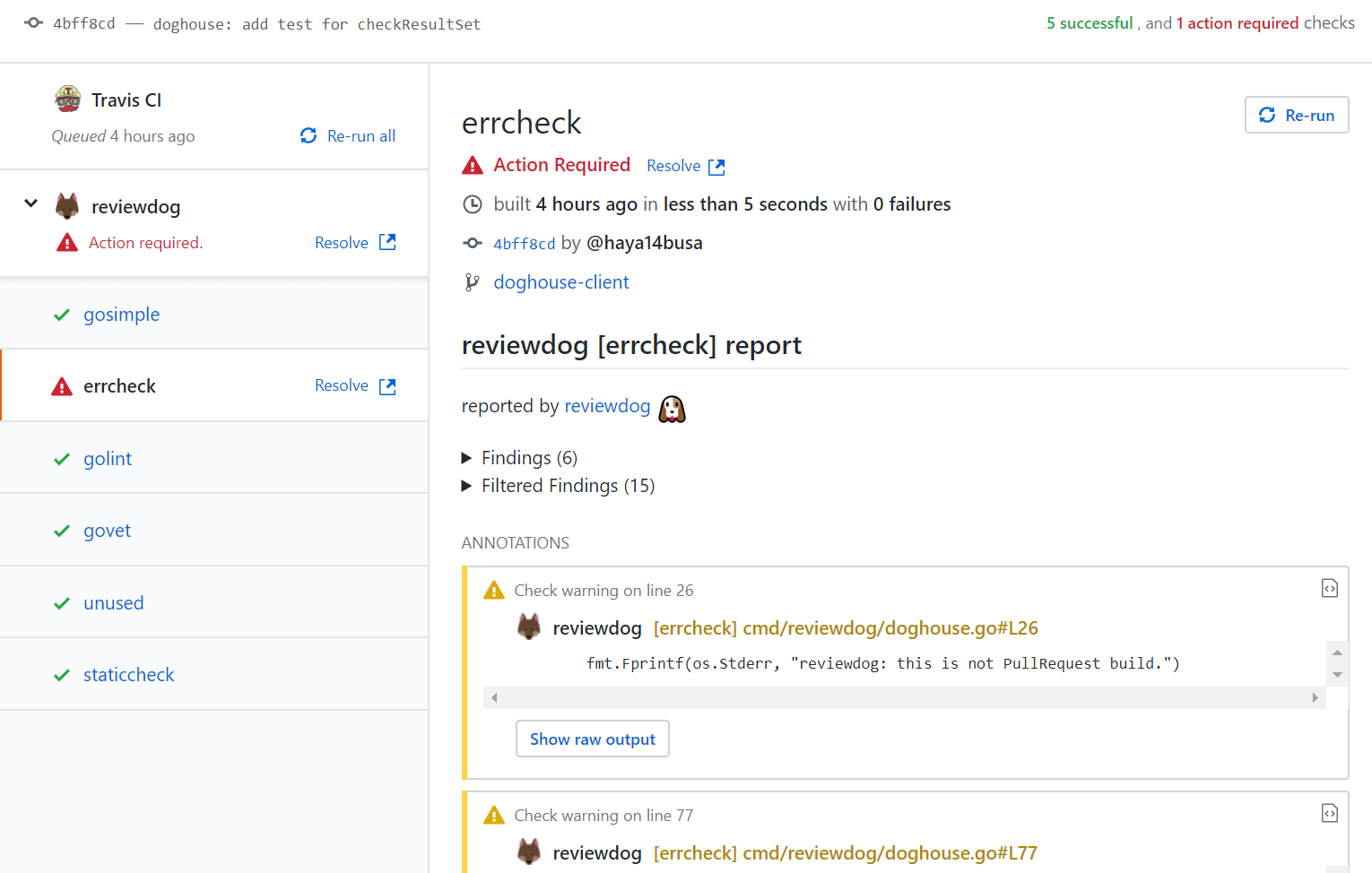
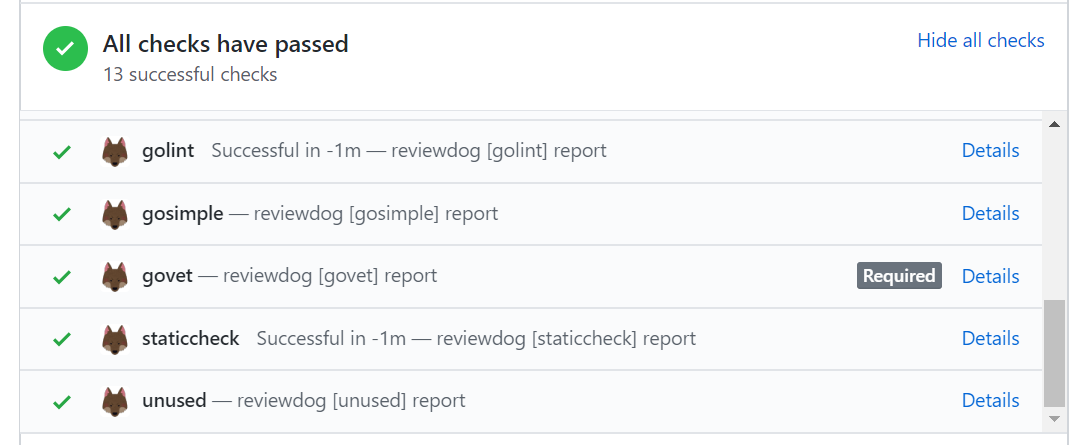
Reporter: GitHub Checks (-reporter=github-pr-check)
github-pr-check reporter reports results to GitHub Checks.
You can change the report level for this reporter by level field in config
file or -level flag. You can control GitHub status
check results with this feature. (default: error)
| Level | GitHub Status |
|---|---|
info | neutral |
warning | neutral |
error | failure |
There are two options to use this reporter.
Option 1) Run codebase from GitHub Actions w/ secrets.GITHUB_TOKEN
Example: .github/workflows/codebase.yml
- name: Run codebase
env:
CODEBASE_GITHUB_API_TOKEN: ${{ secrets.GITHUB_TOKEN }}
run: |
golint ./... | codebase -f=golint -reporter=github-pr-check
See GitHub Actions section too. You can also use public codebase GitHub Actions.
Option 2) Install codebase GitHub Apps
codebase CLI sends a request to codebase GitHub App server and the server post results as GitHub Checks, because Check API is only supported for GitHub App and GitHub Actions.
- Install codebase Apps. https://github.com/apps/codebase
- Set
CODEBASE_TOKENor run codebase CLI in trusted CI providers.
- Get token from
https://codebase.app/gh/{owner}/{repo-name}.
$ export CODEBASE_TOKEN="<token>"
$ codebase -reporter=github-pr-check
Note: Token is not required if you run codebase in Travis or AppVeyor.
Caution
As described above, github-pr-check reporter with Option 2 depends on codebase GitHub App server. The server is running with haya14busa's pocket money for now and I may break things, so I cannot ensure that the server is running 24h and 365 days.
UPDATE: Started getting support by opencollective and GitHub sponsor. See Supporting codebase
You can use github-pr-reviewe reporter or use run codebase under GitHub Actions if you don't want to depend on codebase server.
Reporter: GitHub Checks (-reporter=github-check)
It's basically the same as -reporter=github-pr-check except it works not only for
Pull Request but also for commit.
You can create codebase badge for this reporter.
Reporter: GitHub PullRequest review comment (-reporter=github-pr-reviewe)
github-pr-reviewe reporter reports results to GitHub PullRequest review comments using GitHub Personal API Access Token. GitHub Enterprise is supported too.
- Go to https://github.com/settings/tokens and generate a new API token.
- Check
repofor private repositories orpublic_repofor public repositories.
$ export CODEBASE_GITHUB_API_TOKEN="<token>"
$ codebase -reporter=github-pr-reviewe
For GitHub Enterprise, set the API endpoint by an environment variable.
$ export GITHUB_API="https://example.githubenterprise.com/api/v3/"
$ export CODEBASE_INSECURE_SKIP_VERIFY=true # set this as you need to skip verifying SSL
See GitHub Actions section too if you can use GitHub Actions. You can also use public codebase GitHub Actions.
Reporter: GitLab MergeRequest discussions (-reporter=gitlab-mr-discussion)
Required GitLab version: >= v10.8.0
gitlab-mr-discussion reporter reports results to GitLab MergeRequest discussions using
GitLab Personal API Access token.
Get the token with api scope from https://gitlab.com/profile/personal_access_tokens.
$ export CODEBASE_GITLAB_API_TOKEN="<token>"
$ codebase -reporter=gitlab-mr-discussion
The CI_API_V4_URL environment variable, defined automatically by Gitlab CI (v11.7 onwards), will be used to find out the Gitlab API URL.
Alternatively, GITLAB_API can also be defined, in which case it will take precedence over CI_API_V4_URL.
$ export GITLAB_API="https://example.gitlab.com/api/v4"
$ export CODEBASE_INSECURE_SKIP_VERIFY=true # set this as you need to skip verifying SSL
Reporter: GitLab MergeRequest commit (-reporter=gitlab-mr-commit)
gitlab-mr-commit is similar to gitlab-mr-discussion reporter but reports results to each commit in GitLab MergeRequest.
gitlab-mr-discussion is recommended, but you can use gitlab-mr-commit reporter if your GitLab version is under v10.8.0.
$ export CODEBASE_GITLAB_API_TOKEN="<token>"
$ codebase -reporter=gitlab-mr-commit
Reporter: Gerrit Change review (-reporter=gerrit-change-review)
gerrit-change-review reporter reports results to Gerrit Change using Gerrit Rest APIs.
The reporter supports Basic Authentication and Git-cookie based authentication for reporting results.
Set GERRIT_USERNAME and GERRIT_PASSWORD environment variables for basic authentication, and put GIT_GITCOOKIE_PATH for git cookie-based authentication.
$ export GERRIT_CHANGE_ID=changeID
$ export GERRIT_REVISION_ID=revisionID
$ export GERRIT_BRANCH=master
$ export GERRIT_ADDRESS=http://<gerrit-host>:<gerrit-port>
$ codebase -reporter=gerrit-change-review
Reporter: Bitbucket Code Insights Reports (-reporter=bitbucket-code-report)
bitbucket-code-report generates the annotated Bitbucket Code Insights report.
For now, only the no-filter mode is supported, so the whole project is scanned on every run.
Reports are stored per commit and can be viewed per commit from Bitbucket Pipelines UI or
in Pull Request. In the Pull Request UI affected code lines will be annotated in the diff,
as well as you will be able to filter the annotations by This pull request or All.
If running from Bitbucket Pipelines, no additional configuration is needed (even credentials). If running locally or from some other CI system you would need to provide Bitbucket API credentials:
- For Basic Auth you need to set the following env variables:
BITBUCKET_USERandBITBUCKET_PASSWORD - For AccessToken Auth you need to set
BITBUCKET_ACCESS_TOKEN
$ export BITBUCKET_USER="my_user"
$ export BITBUCKET_PASSWORD="my_password"
$ codebase -reporter=bitbucket-code-report
To post a report to the Bitbucket Server use BITBUCKET_SERVER_URL variable:
$ export BITBUCKET_USER="my_user"
$ export BITBUCKET_PASSWORD="my_password"
$ export BITBUCKET_SERVER_URL="https://bitbucket.my-company.com"
$ codebase -reporter=bitbucket-code-report
Supported CI services
GitHub Actions
Example: .github/workflows/codebase.yml
name: codebase
on: [pull_request]
jobs:
codebase:
name: codebase
runs-on: ubuntu-latest
steps:
# ...
- uses: codebase/action-setup@v1
with:
codebase_version: latest # Optional. [latest,nightly,v.X.Y.Z]
- name: Run codebase
env:
CODEBASE_GITHUB_API_TOKEN: ${{ secrets.GITHUB_TOKEN }}
run: |
codebase -reporter=github-pr-check -runners=golint,govet
# or
codebase -reporter=github-pr-reviewe -runners=golint,govet
Example (github-check reporter):
Only github-check reporter can run on the push event too.
name: codebase (github-check)
on:
push:
branches:
- master
pull_request:
jobs:
codebase:
name: codebase
runs-on: ubuntu-latest
steps:
# ...
- name: Run codebase
env:
CODEBASE_GITHUB_API_TOKEN: ${{ secrets.GITHUB_TOKEN }}
run: |
codebase -reporter=github-check -runners=golint,govet
Public Codebase GitHub Actions
You can use public GitHub Actions to start using codebase with ease! :tada: :arrow_forward: :tada:
- Common
- Text
- codebase/action-alex - Run alex which catches insensitive, inconsiderate writing. (e.g. master/slave)
- codebase/action-languagetool - Run languagetool.
- tsuyoshicho/action-textlint - Run textlint
- tsuyoshicho/action-redpen - Run redpen
- Markdown
- Docker
- codebase/action-hadolint - Run hadolint to lint
Dockerfile.
- codebase/action-hadolint - Run hadolint to lint
- Env
- dotenv-linter/action-dotenv-linter - Run dotenv-linter to lint
.envfiles.
- dotenv-linter/action-dotenv-linter - Run dotenv-linter to lint
- Shell script
- codebase/action-shellcheck - Run shellcheck.
- codebase/action-shfmt - Run shfmt.
- Go
- codebase/action-staticcheck - Run staticcheck.
- codebase/action-golangci-lint - Run golangci-lint and supported linters individually by golangci-lint.
- JavaScript
- codebase/action-eslint - Run eslint.
- TypeScript
- EPMatt/codebase-action-tsc - Run tsc.
- CSS
- Vim script
- codebase/action-vint - Run vint.
- tsuyoshicho/action-vimlint - Run vim-vimlint
- Terraform
- codebase/action-tflint - Run tflint.
- YAML
- codebase/action-yamllint - Run yamllint.
- Ruby
- codebase/action-brakeman - Run brakeman.
- codebase/action-reek - Run reek.
- codebase/action-rubocop - Run rubocop.
- vk26/action-fasterer - Run fasterer.
- PrintReleaf/action-standardrb - Run standardrb.
- tk0miya/action-erblint - Run erb-lint
- tk0miya/action-steep - Run steep
- blooper05/action-rails_best_practices - Run rails_best_practices
- tomferreira/action-bundler-audit - Run bundler-audit
- Python
- wemake-python-styleguide - Run wemake-python-styleguide
- tsuyoshicho/action-mypy - Run mypy
- jordemort/action-pyright - Run pyright
- dciborow/action-pylint - Run pylint
- codebase/action-black - Run black
- Kotlin
- ScaCap/action-ktlint - Run ktlint.
- Android Lint
- Ansible
- GitHub Actions
- Protocol Buffers
... and more on GitHub Marketplace.
Missing actions? Check out codebase/action-template and create a new codebase action!
Please open a Pull Request to add your created codebase actions here :sparkles:. I can also put your repositories under codebase org and co-maintain the actions. Example: action-tflint.
Graceful Degradation for Pull Requests from forked repositories

GITHUB_TOKEN for Pull Requests from a forked repository doesn't have write
access to Check API nor Review API due to GitHub Actions
restriction.
Instead, codebase uses Logging commands of GitHub
Actions
to post results as
annotations
similar to github-pr-check reporter.
Note that there is a limitation for annotations created by logging commands, such as max # of annotations per run. You can check GitHub Actions log to see full results in such cases.
codebase badge 
As github-check reporter support running on commit, we can create codebase
GitHub Action badge
to check the result against master commit for example. :tada:
Example:
<!-- Replace <OWNER> and <REPOSITORY>. It assumes workflow name is "codebase" -->
[](https://github.com/<OWNER>/<REPOSITORY>/actions?query=workflow%3Acodebase+event%3Apush+branch%3Amaster)
Travis CI
Travis CI (-reporter=github-pr-check)
If you use -reporter=github-pr-check in Travis CI, you don't need to set CODEBASE_TOKEN.
Example:
install:
- mkdir -p ~/bin/ && export PATH="~/bin/:$PATH"
- curl -sfL https://raw.githubusercontent.com/khulnasoft/codebase/master/install.sh| sh -s -- -b ~/bin
script:
- codebase -conf=.codebase.yml -reporter=github-pr-check
Travis CI (-reporter=github-pr-reviewe)
Store GitHub API token by travis encryption keys.
$ gem install travis
$ travis encrypt CODEBASE_GITHUB_API_TOKEN=<token> --add env.global
Example:
env:
global:
- secure: <token>
install:
- mkdir -p ~/bin/ && export PATH="~/bin/:$PATH"
- curl -sfL https://raw.githubusercontent.com/khulnasoft/codebase/master/install.sh| sh -s -- -b ~/bin
script:
- >-
golint ./... | codebase -f=golint -reporter=github-pr-reviewe
Examples
Circle CI
Store CODEBASE_GITHUB_API_TOKEN (or CODEBASE_TOKEN for github-pr-check) in
Environment variables - CircleCI
.circleci/config.yml sample
version: 2
jobs:
build:
docker:
- image: golang:latest
steps:
- checkout
- run: curl -sfL https://raw.githubusercontent.com/khulnasoft/codebase/master/install.sh| sh -s -- -b ./bin
- run: go vet ./... 2>&1 | ./bin/codebase -f=govet -reporter=github-pr-reviewe
# Deprecated: prefer GitHub Actions to use github-pr-check reporter.
- run: go vet ./... 2>&1 | ./bin/codebase -f=govet -reporter=github-pr-check
GitLab CI
Store CODEBASE_GITLAB_API_TOKEN in GitLab CI variable.
.gitlab-ci.yml sample
codebase:
script:
- codebase -reporter=gitlab-mr-discussion
# Or
- codebase -reporter=gitlab-mr-commit
Bitbucket Pipelines
No additional configuration is needed.
bitbucket-pipelines.yml sample
pipelines:
default:
- step:
name: Codebase
image: golangci/golangci-lint:v1.31-alpine
script:
- wget -O - -q https://raw.githubusercontent.com/khulnasoft/codebase/master/install.sh |
sh -s -- -b $(go env GOPATH)/bin
- golangci-lint run --out-format=line-number ./... | codebase -f=golangci-lint -reporter=bitbucket-code-report
Common (Jenkins, local, etc...)
You can use codebase to post review comments from anywhere with following environment variables.
| name | description |
|---|---|
CI_PULL_REQUEST | Pull Request number (e.g. 14) |
CI_COMMIT | SHA1 for the current build |
CI_REPO_OWNER | repository owner (e.g. "codebase" for https://github.com/khulnasoft/codebase/errorformat) |
CI_REPO_NAME | repository name (e.g. "errorformat" for https://github.com/khulnasoft/codebase/errorformat) |
CI_BRANCH | [optional] branch of the commit |
$ export CI_PULL_REQUEST=14
$ export CI_REPO_OWNER=haya14busa
$ export CI_REPO_NAME=codebase
$ export CI_COMMIT=$(git rev-parse HEAD)
and set a token if required.
$ CODEBASE_TOKEN="<token>"
$ CODEBASE_GITHUB_API_TOKEN="<token>"
$ CODEBASE_GITLAB_API_TOKEN="<token>"
If a CI service doesn't provide information such as Pull Request ID - codebase can guess it by a branch name and commit SHA.
Just pass the flag guess:
$ codebase -conf=.codebase.yml -reporter=github-pr-check -guess
Jenkins with GitHub pull request builder plugin
- GitHub pull request builder plugin - Jenkins - Jenkins Wiki
- Configuring a GitHub app account - Jenkins - CloudBees - required to use github-pr-check formatter without codebase server or GitHub actions.
$ export CI_PULL_REQUEST=${ghprbPullId}
$ export CI_REPO_OWNER=haya14busa
$ export CI_REPO_NAME=codebase
$ export CI_COMMIT=${ghprbActualCommit}
$ export CODEBASE_INSECURE_SKIP_VERIFY=true # set this as you need
# To submit via codebase server using github-pr-check reporter
$ CODEBASE_TOKEN="<token>" codebase -reporter=github-pr-check
# Or, to submit directly via API using github-pr-reviewe reporter
$ CODEBASE_GITHUB_API_TOKEN="<token>" codebase -reporter=github-pr-reviewe
# Or, to submit directly via API using github-pr-check reporter (requires GitHub App Account configured)
$ CODEBASE_SKIP_DOGHOUSE=true CODEBASE_GITHUB_API_TOKEN="<token>" codebase -reporter=github-pr-check
Exit codes
By default codebase will return 0 as exit code even if it finds errors.
If -fail-on-error flag is passed, codebase exits with 1 when at least one error was found/reported.
This can be helpful when you are using it as a step in your CI pipeline and want to mark the step failed if any error found by linter.
See also -level flag for github-pr-check/github-check reporters.
codebase will exit with 1 if reported check status is failure as well if -fail-on-error=true.
Filter mode
codebase filter results by diff and you can control how codebase filter results by -filter-mode flag.
Available filter modes are as below.
added (default)
Filter results by added/modified lines.
diff_context
Filter results by diff context. i.e. changed lines +-N lines (N=3 for example).
file
Filter results by added/modified file. i.e. codebase will report results as long as they are in added/modified file even if the results are not in actual diff.
nofilter
Do not filter any results. Useful for posting results as comments as much as possible and check other results in console at the same time.
-fail-on-error also works with any filter-mode and can catch all results from any linters with nofilter mode.
Example:
$ codebase -reporter=github-pr-reviewe -filter-mode=nofilter -fail-on-error
Filter Mode Support Table
Note that not all reporters provide full support for filter mode due to API limitation.
e.g. github-pr-reviewe reporter uses GitHub Review
API and GitHub Review
Comment API but these APIs don't support posting comments outside diff file,
so codebase will use Check annotation as fallback to post those comments [1].
-reporter \ -filter-mode | added | diff_context | file | nofilter |
|---|---|---|---|---|
local | OK | OK | OK | OK |
github-check | OK | OK | OK | OK |
github-pr-check | OK | OK | OK | OK |
github-pr-reviewe | OK | OK | OK | Partially Supported [1] |
gitlab-mr-discussion | OK | OK | OK | Partially Supported [2] |
gitlab-mr-commit | OK | Partially Supported [2] | Partially Supported [2] | Partially Supported [2] |
gerrit-change-review | OK | OK? [3] | OK? [3] | Partially Supported? [2][3] |
bitbucket-code-report | NO [4] | NO [4] | NO [4] | OK |
gitea-pr-review | OK | OK | Partially Supported [2] | Partially Supported [2] |
- [1] Report results that are outside the diff file with Check annotation as fallback if it's running in GitHub actions instead of Review API (comments). All results will be reported to console as well.
- [2] Report results that are outside the diff file to console.
- [3] It should work, but not been verified yet.
- [4] Not implemented at the moment
Debugging
Use the -tee flag to show debug info.
codebase -filter-mode=nofilter -tee
Articles
- codebase — A code review dog who keeps your codebase healthy
- codebase ♡ GitHub Check — improved automated review experience
- Automated Code Review on GitHub Actions with codebase for any languages/tools
- GitHub Actions to guard your workflow
:bird: Author
Contributors
Supporting codebase
Become GitHub Sponsor for each contributor or become a backer or sponsor from opencollective.